Exp 3: Exploring Windows Firewall Security
Exp 3: Exploring Windows
Firewall Security
Aim:
To
study and explore about the windows firewall security and observe the
performance of system with firewall and without firewalls
Software
Requirement: Two Computer Systems, Windows 10,Internet Access, Super Scan
Step1 :Opening Windows Firewall
· Select Windows Firewall in Control Panel
Step 2: Configure the firewall
· Be sure that the firewall is On
· Check which programs and services are permitted (Exceptions tab)
· Check the ICMP settings (Advanced tab)
Step 3: Test
the firewall
What
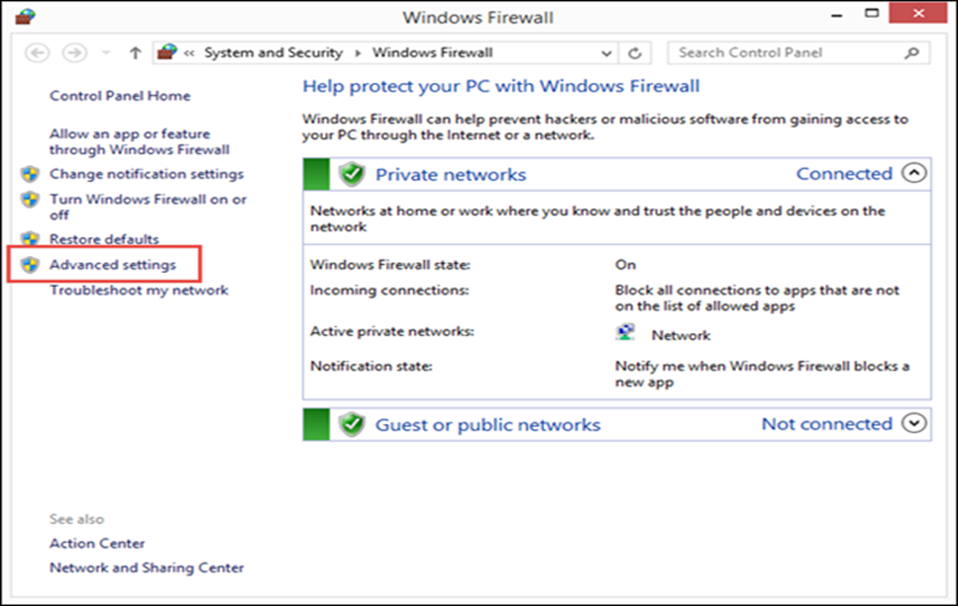
is Windows Firewall with Advanced Settings?
Windows Firewall with
Advanced Security is a management snap-in for the Windows Firewall from which
you can control in all the rules and exceptions that govern how the Windows
Firewall works. In order to access it, you need to open the Windows Firewall as
shown in the previous lesson and then click or tap the “Advanced settings” link
on the column on the left.
Figure 1
Understanding Inbound,
Outbound & Connection Security Rules in Firewall
In Windows Firewall with
Advanced Security you will encounter three important types of rules:
·
Inbound rules – they apply to traffic
that is coming from the network or the Internet to your Windows computer or
device. For example, if you are downloading a file through BitTorrent, the
download of that file is filtered through an inbound rule.
·
Outbound rules – these rules apply to
traffic that is originating from your computer and going to the network and the
Internet. For example, your request to load the How-To Geek website in your web
browser is outbound traffic and it is filtered through an outbound rule. When the
website is downloaded and loaded by your browser, this is inbound traffic.
· Connection security rules –less common rules that are used to secure the traffic between two specific computers while it crosses the network. This type of rule is used in very controlled environments with special security requirements.
Figure
2
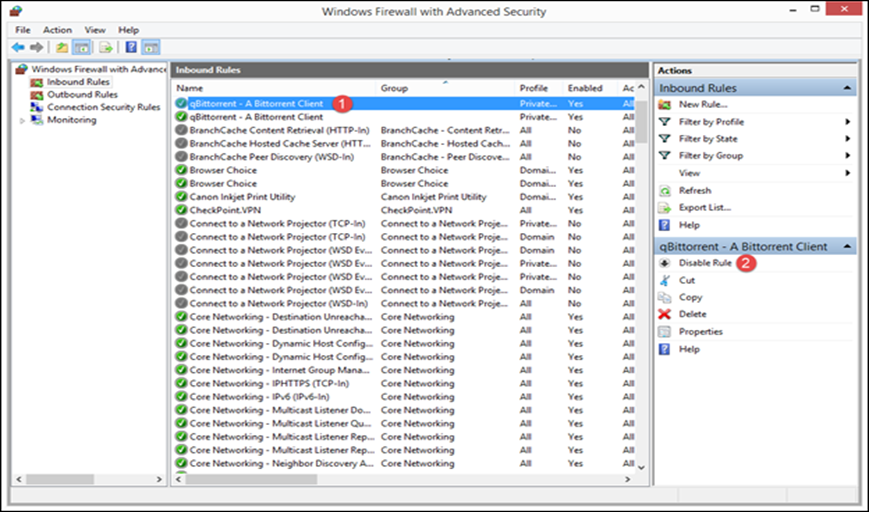
You will see lots of inbound and
outbound rules. Some rules will have a green checkmark near their name while
others will have a gray one. The rules with the green checkmark are enabled,
meaning that they are used by Windows Firewall. Those with a gray checkmark are
disabled and they are not used by Windows Firewall.
What
Can Be Monitored from the Windows Firewall with Advanced Security?
Besides the three types of rules mentioned earlier, you will find a section named “Monitoring.” If you expand it, you can view the active firewall rules, the active connection security rules, and view the active security associations.
Figure 3
This is the information maintained about a secure encrypted channel on the local computer or device, so that this information can be used for future network traffic to a specific remote computer or device. Here you can view which peers are currently connected to your computer and which protection suite was used by Windows to form the security association.
How
to Manage Existing Windows Firewall Rules?
When working with the rules that are built into the Windows Firewall is that it is better to disable a rule than delete it. In case you do something ill-advised, then it is very easy to repair everything by re-enabling disabled rules. Rules which get deleted cannot be recovered unless you restore all the Windows Firewall settings to their defaults.
Figure 4
In order to edit a rule and check the way it works, just by double-clicking on it, selecting it, and then pressing “Properties” in the column on the right. All the parameters we have mentioned can be modified in the “Properties” window of that rule.
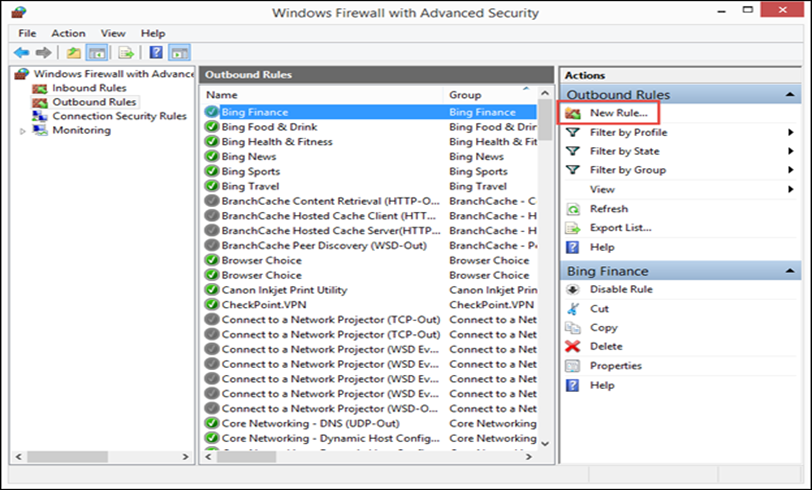
How
to Create an Inbound Rule for the Windows Firewall?
Let’s go to “Inbound Rules” and press “New Rule” in the column on the right. We have created a rule which blocks all inbound traffic made using the TCP protocol on the port 30770.
Figure 5
Choices are:
·
Program – the rule applies to a
specific program
·
Port – the rule applies to
the network traffic that is performed through a specific port
·
Predefined – rule that controls
the connections performed by a specific Windows service or feature
·
Custom – a custom rule that
can block both programs and ports or a specific combination of both.
Figure 6
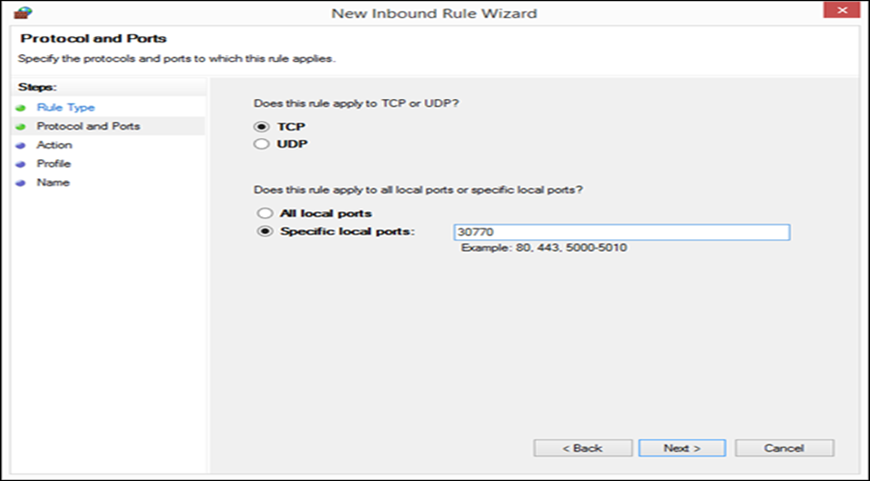
Now we
are asked to select the protocol for which the rule applies and the port. The
choices for protocols are TCP and UDP. If you want a rule that applies to both,
you need to create two rules, one for each protocol. Then, we had the choice to
block all ports or only specific ones. We selected “Specific local ports”,
entered “30770,” and pressed “Next.”
Figure 7
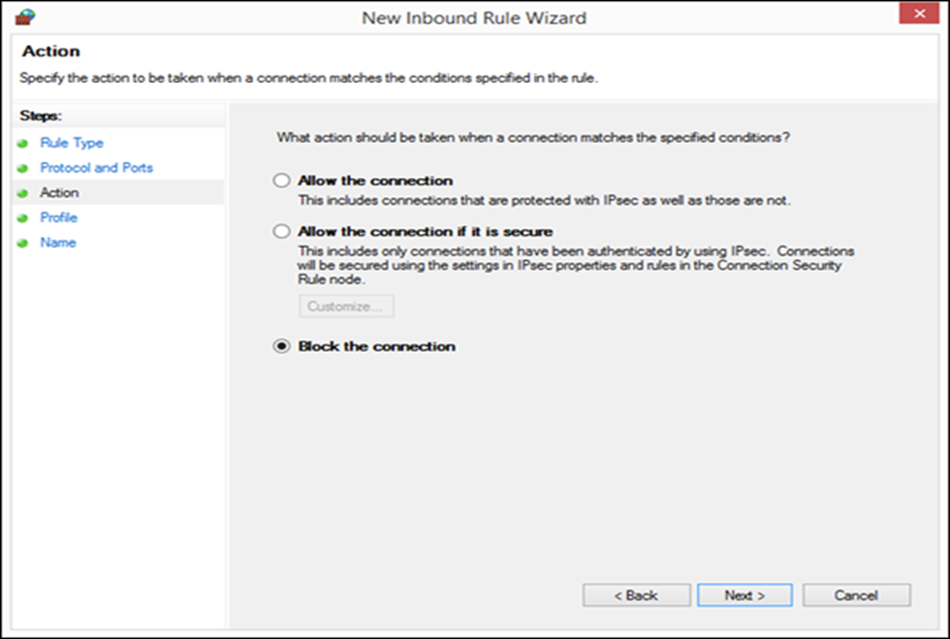
Now you are asked to select what action to take when a connection matches the conditions specified earlier. For our example, we have chosen “Block the connection” and pressed “Next.”
Figure 8
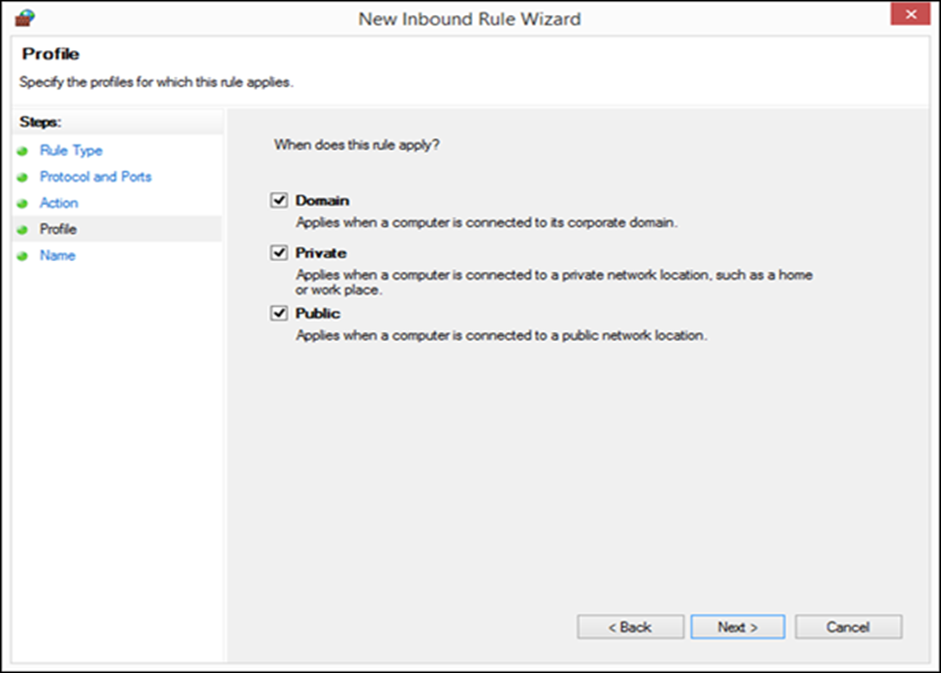
Now
you have to select the network locations for which the rule applies. Since we
wanted to block all TCP traffic on port 30770, we selected all three locations
and pressed “Next.”
Figure 9
Now
you are asked to select when the rule applies. This means the network location
when the rule is applied:
·
Domain – the
rule is applied only when the computer is connected to a network domain
·
Private – the
rule is applied only when the computer is connected to trusted private networks
·
Public – the
rule is applied only when the computer is connected to untrusted public
networks
Finally, enter the name and the description for the newly created rule and press “Finish.”
Figure 10
In the similar process to Inbound, the outbound rules can also be created for Allowing, Blocking a program from the System.
Conclusion:
Hence Windows
based firewall tool has been studied and the performance of the systems are
analyzed successfully.
REFERENCES
1.
https://github.com/sharanyavenkat25/Cryptanalysis-TranspositionCiphers/blob/master/project.py
Fetched: 2022-06-10T08:21:22.8600000
2.
https://www.nyit.edu/files/its/SC_Peoplesoft_PopUpBlockerInstructions.pdf
Fetched: 2022-06-10T08:21:31.6500000
3.
http://www.seattle.gov/documents/Departments/FAS/PublicDisclosure/PRRC_troubleshooting.
pdf Fetched: 2022-06-10T08:20:56.0630000
4.
https://eweb4.ccf.org/onlinelearning/browserDetect/BrowserDirections.htm?
txtBrowser=Chrome Fetched: 2022-06-10T08:20:55.7570000
5. URL: https://support.microsoft.com/en-us/windows/delete-and-manage-cookies-168dab11-0753-
043d-7c16-ede5947fc64d Fetched: 2021-05-07T10:49:08.8870000




Comments
Post a Comment